How many times have you entered or reset a password today? In many companies, handling access data is still a daily struggle. Despite all security precautions, passwords remain a risk factor: they are forgotten, reused, chosen unsafely, or compromised.
But that could soon change fundamentally.
Passkeys are set to permanently change the way we authenticate ourselves digitally. Major platforms such as Apple, Google, and Microsoft are already actively supporting the technology.
In 2025, technological potential has become a concrete standard. More and more companies are considering introducing it or are already implementing it.
But what exactly are passkeys? How do they work, and what do passkeys mean for your company, your employees, and your security strategy?
This article provides a well-founded introduction to the topic, explained in an understandable way and with a clear view of the opportunities and requirements for business practice.
What are passkeys?
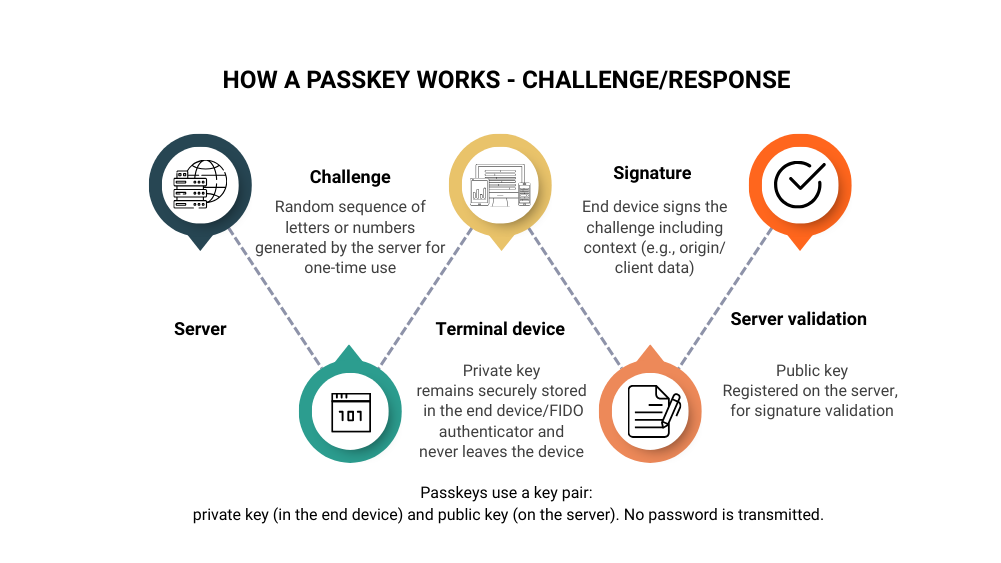
Passkeys are a secure authentication method that makes traditional passwords obsolete. Technically, they are based on a proven principle: public key cryptography combined with a challenge-response procedure. The basis is the Web Authentication Protocol, or WebAuthn for short. This uses a digital key pair consisting of a public key and a private key.
Key pair creation:
- When you set up an account with passkeys, a private key is stored on your device (e.g., smartphone or laptop).
- A corresponding public key is stored on the service provider's server.
Login:
- When you log in, the server sends a request (challenge) to your device.
- Your device signs this request using the private key and sends the response back.
- The server verifies the signature with the public key to confirm your identity.
Security factor:
- To ensure that only you have access, the release of the passkey is confirmed by an additional security factor such as a fingerprint, facial recognition, or PIN.
A key advantage: The shared secret (sender and recipient know the password) that exists with traditional passwords is completely eliminated. Passkeys cannot therefore be intercepted, guessed, or reused. This is a key security benefit.
The technology behind passkeys is based on open standards such as FIDO2 and is already supported by platforms such as Apple (iCloud Keychain), Google (Passkey Manager), and Microsoft (Windows Hello). Companies can increasingly integrate passkeys into existing IAM and SSO solutions.
What makes passkeys so secure?
The security of passkeys is based on a fundamentally different principle than traditional passwords. While passwords rely on storing and entering a shared secret, which makes them vulnerable to phishing, brute force attacks, and data leaks, passkeys work without ever storing or transmitting a password.
1. Phishing resistance through cryptographic binding
Passkeys are bound to the domain of the application for which they were created. This means that even if a user is redirected to a fake website, the authentication process cannot be completed because the private key is linked exclusively to the real domain. This effectively prevents phishing.
2. No central password databases
Since no passwords are stored or transmitted, there is no need for central password storage, which is a frequent target of cyberattacks. Even if an attack on the server is successful, passkeys are useless to attackers because they are worthless without the private key on the user's device.
3. Protection against credential stuffing and password recycling
Passkeys are unique and account-specific. There is no concept of “the same password on multiple platforms.” This eliminates attack vectors such as credential stuffing, where compromised credentials from previous leaks are automatically tested.
4. Strong security through hardware and biometrics
Authentication takes place locally on the device, often using biometric features (Face ID, fingerprint) or device locks. The private key never leaves the device. This means that access to the device and identity verification are closely linked.
5. Proven standards and broad support
Passkeys are based on the FIDO2 standard, which was developed jointly by the FIDO Alliance and the World Wide Web Consortium (W3C). The underlying cryptography is considered highly secure, is continuously being further developed, and has already proven itself in millions of authentications worldwide.
💡 SoftGuide Infobox
Passkeys – more secure than passwords
- How it works: based on asymmetric cryptography, local identity verification, and device binding
- Advantage for companies: significantly higher security
- Additional benefits: lower risk of human error (e.g., weak or reused passwords)
What does this mean for your users?
For most users, dealing with passwords is a daily challenge, whether it's forgotten login details, cumbersome reset processes, or insecure sticky note solutions. Passkeys provide noticeable relief here, both for end users and IT support teams.
1. Log in without entering a password
Passkeys make logging in easy, fast, and secure, for example by unlocking the device with a fingerprint, facial recognition, or device PIN. The technical complexity runs in the background. For users, logging in feels seamless and convenient.
2. No forgetting, no resetting
Since no password needs to be assigned or remembered, one of the most common causes of support tickets is eliminated: resetting access data. This not only reduces frustration among employees, but also saves considerable resources in IT support.
3. A login experience across all devices
Many passkey solutions allow the private key to be synchronized across devices, for example via iCloud Keychain on Apple or Google Passkey Manager. It is also possible to use a cross-platform password manager with a passkey function. This allows users to log in to new devices without having to set them up again, securely and user-friendly.
4. Greater acceptance thanks to intuitive operation
Unlike complex multi-factor solutions or token systems, the use of passkeys is intuitive and familiar to users, for example through biometric unlocking, which is already established on most smartphones. This increases acceptance and reduces training costs.
💡 SoftGuide Infobox
Passkeys offer:
- A modern, accessible login experience
- High security
For companies, this means:
- Less friction
- More productivity
- Higher satisfaction
What happens if a device is lost, stolen, or defective?
A common scenario in everyday business life: What happens if the device on which a passkey is stored is lost, stolen, or defective?
The good news: Passkeys are designed to remain secure and recoverable even in such cases. This requires the right choice of platform, a structured implementation process, and defined backup strategies. Here is an overview of the most important aspects from an IT and support perspective:
Synchronization via cloud services
On most platforms, passkeys are synchronized via the user account – for example, via:
- Apple iCloud Keychain
- Google Password Manager
- Third-party providers such as 1Password or Dashlane
The advantage: Access to accounts is retained even if the original device is no longer available – provided that another device is linked or access to the cloud account exists.
Protection against theft
Even if stolen, a device is worthless without biometric unlocking (fingerprint, facial recognition) or a PIN. Additional security is provided by remote locking or deletion functions, such as “Find My iPhone” or “Find My Device” on Android.
Recovery when changing devices
When switching to a new or replacement device, it is often sufficient to log in to the respective user account. Passkeys are then synchronized automatically. Providers such as Apple also offer:
- Account recovery contact
- Keychain recovery via escrow
Device management in a corporate context
In companies with mobile device management (MDM) or endpoint management solutions, it is possible to:
- Remotely deactivate or delete lost devices
- Provision new devices and synchronize them automatically
- Reassign access rights via the IAM system
Access can thus be restored in a structured and secure manner without resetting passwords.
Define fallback strategies
For critical roles or particularly sensitive areas, companies should plan additional recovery mechanisms:
- Registration of multiple devices per user
- Use of alternative authentication methods (e.g., FIDO2 security keys)
- Administrative recovery processes via help desk or IAM systems
Be aware of technical limitations
- Locally stored passkeys (e.g., on a USB security key without cloud sync) cannot be recovered if no backup exists.
- Changing ecosystems (e.g., from Android to Apple) can be problematic if no cross-platform solution is used.
💡 SoftGuide Infobox
Passkey recovery at a glance
- Device loss ≠ access loss: Passkeys remain protected.
- Secure recovery: Via cloud services or central IT management solutions.
- Success factor: Plan recovery and fallback strategies from the outset in terms of technology, organization, and communication.
Use in companies – opportunities
The introduction of passkeys is more than just a technical update; it is a strategic step toward a future-proof, user-friendly, and scalable authentication landscape. Companies that adopt passwordless procedures early on benefit in several ways: operationally, in terms of security, and economically.
1. Reduction in support costs and operating expenses
Password resets are among the most common IT support requests. According to industry studies, they not only cause high internal costs, but also impair employee productivity. With passkeys, these requests are almost completely eliminated.
2. Strengthening of the security architecture
Passkeys eliminate several areas of vulnerability at once:
- No phishing, as no secret is entered
- No credential stuffing, as there are no reusable access data
- No central password repository that can be tapped
In combination with existing security mechanisms such as single sign-on (SSO) or zero trust architectures, passkeys can become the basis of a modern, resilient IT security strategy.
3. Positive user experience & high acceptance
User-friendly authentication methods promote compliance with security policies. If a secure method is easy to use, it will also be used. Passkeys are proving to be extremely practical, especially in companies with mobile workplaces or BYOD (Bring Your Own Device) strategies.
4. Easy integration into existing systems
Leading providers of identity and access management (IAM) systems such as Okta, Microsoft Entra ID (formerly Azure AD), and Ping Identity already support FIDO2-based authentication, often in conjunction with mobile devices or hardware tokens.
For a successful rollout, companies should:
- Analyze their device fleet: Are there devices that support biometric unlocking?
- Adapt identity management: Is the identity provider already FIDO2-enabled?
- Involve users in a targeted manner: Is the rollout accompanied by communication and support?
In short, passkeys offer companies the opportunity to improve security, user-friendliness, and efficiency in equal measure. The technology is ready, and the time for change has never been more favorable than now.
Conclusion – Passkeys are more than just a trend
The challenges surrounding password security, user acceptance, and IT support are well known, and they cost companies time, money, and security every day. Passkeys offer a real paradigm shift here.
They combine high security with an intuitive user experience and enable a modern, scalable authentication strategy. Instead of centrally stored, shared secrets, passkeys rely on asymmetric cryptography, device binding, and biometric unlocking, systematically eliminating common attack vectors such as phishing or credential stuffing.
From an operational perspective, the arguments speak for themselves:
- ✅ Less support effort
- ✅ Higher user satisfaction
- ✅ Compatibility with established IAM and SSO solutions
- ✅ Improved compliance and security
The technology is mature. The standards are set. Integration is possible.
Now is the right time to actively shape the passwordless future. Whether as part of a pilot project, as a supplement to your MFA strategy, or as part of your overall IT transformation, passkeys can be the next logical step on your path to greater security and efficiency.
✅ Find out now: Is your company ready for passkeys?
Our free checklist provides you with a structured assessment of whether your technical requirements, processes, and strategies are ready for passwordless authentication.
- 🔍 17 practical questions
- 📊 Immediately usable for IT, security, and management
- 📥 Available for download as a PDF—free of charge and without obligation