The requirements for secure and user-friendly authentication methods are constantly increasing. Passkeys are a modern, passwordless method based on cryptographic procedures and are considered a promising successor to traditional password systems. They not only offer greater security, but also significantly improved user convenience.
For companies, switching to passkeys is a strategic decision. At the same time, integrating this technology into existing, often heterogeneous IT landscapes poses a complex challenge. This is particularly the case when outdated IT systems (legacy systems) are in use. This article highlights the technical and organizational hurdles involved in introducing passkeys into legacy systems and presents practical solutions.
Basics: Passkeys & legacy systems at a glance
What are passkeys?
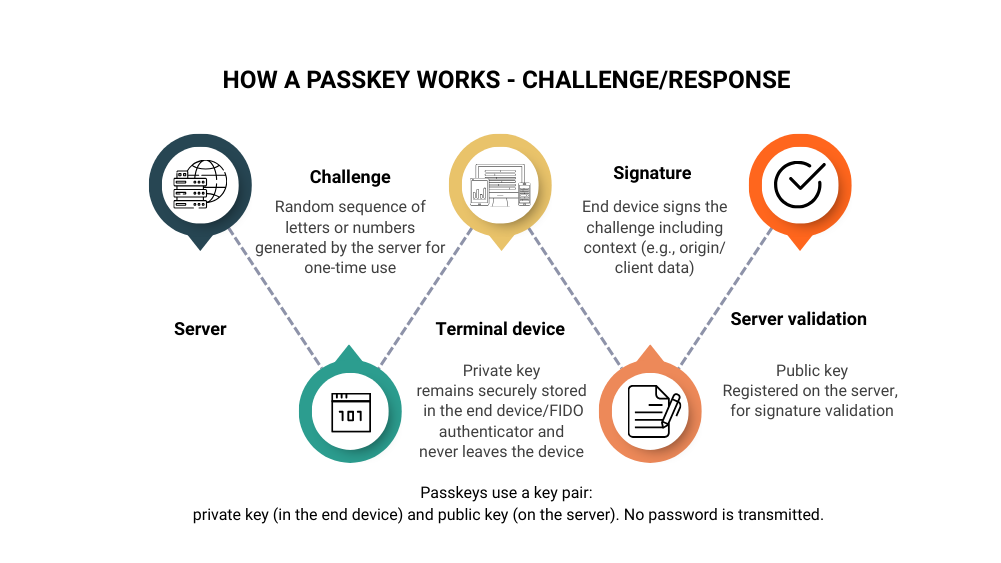
Passkeys are a modern approach to user-friendly and secure authentication based on public key cryptography. Instead of passwords, which are vulnerable to phishing, brute force attacks, or leaks, passkeys use an asymmetric key pair:
- Private key: Stored securely on the user's device (e.g., smartphone, laptop).
- Public key: Stored on the authenticating service (e.g., web application, IT system).
Authentication takes place locally via biometric methods (e.g., fingerprint, facial recognition) or a PIN, without the password ever leaving the end device. This makes passkeys immune to classic password attacks and also offers a much more pleasant user experience.
Passkeys comply with the open FIDO2 standard, which was developed by the FIDO Alliance and the World Wide Web Consortium (W3C) and is increasingly supported by major platforms (Apple, Google, Microsoft).
You can read more about security in the article: “Passkey security – How secure is passwordless login really?”
What are legacy systems?
The term “legacy system” refers to IT systems that have been used in companies for many years and perform business-critical functions, but are no longer up to date in terms of technology. Typical characteristics of such systems are:
- Outdated operating systems and software platforms for which there is no longer any official support or security updates.
- Proprietary interfaces and protocols that make integration with modern services difficult.
- Insufficient documentation or lack of expertise in maintenance and further development.
- Hardware dependencies, such as specialized terminals or control units.
Despite these limitations, legacy systems remain essential in many companies because they support central processes and replacing them would involve high investment and risks.
Why legacy systems often do not support passkeys
Integrating modern authentication technologies such as passkeys into legacy systems is difficult because these systems were developed for other security paradigms. Possible incompatibilities include:
- Lack of support for WebAuthn or FIDO2: Legacy applications typically do not offer compatibility with modern web standards or cryptographic protocols.
- Static authentication methods: Many systems are designed for username/password logins without the option of integrating external authentication services.
- Monolithic architectures: Integrated structures are difficult to expand or modularize.
- Limited expandability: Modifications to the authentication process are technically risky or economically unviable due to a lack of API support or older code bases.
These structural challenges highlight why the integration of passkeys into existing environments requires a targeted strategy and technical bridge solutions.
Challenges of integration into existing IT environments
Technological hurdles
Many legacy systems do not support modern authentication protocols. The IT infrastructure is often based on static user databases with hard-coded passwords. Authentication interfaces are proprietary or completely lacking, making seamless integration of passkey mechanisms nearly impossible.
In addition, technological heterogeneity, different programming languages, and inconsistent data formats complicate integration. Systems with closed architectures, where no external authentication services can be connected, are particularly critical.
Furthermore, technical documentation is often lacking, either due to a lack of knowledge following a change in personnel or due to historically grown IT structures.
Security risks
Legacy systems often work with outdated protocols such as LDAP without TLS, HTTP Basic Auth, or proprietary mechanisms without encryption. These systems pose a significant security risk, especially when they are directly connected to external networks.
Missing updates, unpatched security vulnerabilities, and lack of support exacerbate the danger. The lack of protocols for authentication forwarding or tokenization means that modern security standards cannot be implemented.
Complexity in hybrid operation
The parallel use of passkeys and existing password procedures requires a high degree of coordination. Different authentication sources must be synchronized, permissions must be managed consistently, and identities must be clearly mapped.
This leads to increased administrative overhead in hybrid IT landscapes and increases susceptibility to misconfigurations or redundancies in user management.
User-centric challenges
Although passkeys can significantly improve the user experience, many employees are skeptical about the technology. In particular, when the classic login with username and password is no longer visible, a subjective feeling of “insecurity” arises.
Without a targeted communication strategy and appropriate training, many users lack an understanding of how passkeys work and their advantages. This can lead to acceptance problems that jeopardize the success of the introduction.
Solution approaches for integration into legacy systems
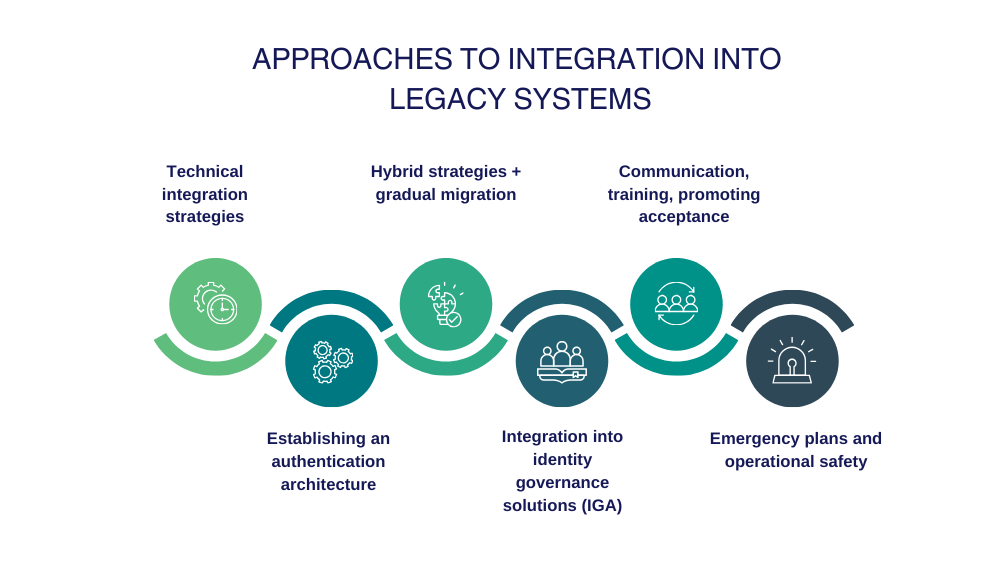
Technical integration strategies
A practical technical approach is to use middleware components that act as an intermediary layer between passkey-enabled systems and legacy applications. These include reverse proxies, API gateways, or identity providers (IdPs) that receive and process authentication requests and translate them into a format that the target system can read.
Example: A FIDO2-compatible identity provider validates the passkey authentication and generates a token that a legacy system accepts as valid authentication (e.g., SAML, LDAP proxy, or Kerberos ticket).
Building a future-proof authentication architecture
In the long term, it is advisable to strategically build a uniform and modular authentication infrastructure. This should have the following characteristics:
- Compatibility with modern standards (FIDO2, OIDC, SAML)
- Central management of identities and policies
- Extensibility for additional authentication methods
Decoupling authentication from individual applications improves maintainability and increases future-proofing.
Hybrid strategies and gradual migration
Since it is often not possible to completely replace legacy systems in the short term, a hybrid approach is a good option. Passkeys are introduced where they can be used immediately (e.g., in modern web portals), while legacy systems remain accessible via traditional logins.
A phased rollout by department, region, or application class reduces technical risks and increases user acceptance.
Integration into identity governance solutions (IGA)
Modern IGA platforms enable central control and monitoring of identities, roles, and access rights. Integrating passkey procedures into these systems creates consistency and reduces the likelihood of errors in authorization management.
In addition, the use of passkeys can be defined as a compliance criterion for particularly sensitive resources and regularly checked via audits.
💡 SoftGuide Infobox
What is an identity governance solution (IGA)?
Identity governance solutions (IGA) are specialized platforms for the centralized management and control of user identities and access rights within companies. They ensure that employees, partners, and service providers always have exactly the access rights they need to perform their tasks.
Core functions of IGA solutions:
- Management of the entire identity lifecycle (onboarding, role changes, offboarding)
- Control and documentation of access rights for systems, data, and applications
- Automated workflows for assigning, reviewing, and revoking permissions
- Traceable logging of all rights changes (audit trail)
- Support for regulatory compliance (e.g., GDPR, SOX)
- Regular review and recertification of permissions
Benefits for companies:
- Increased security by minimizing access risks
- Increased efficiency through automation of administrative tasks
- Central enforcement and control of compliance requirements
Practical relevance:
IGA plays a central role, especially when switching to modern authentication methods such as passkeys: It enables consistent, audit-proof management and monitoring of access rights, even in complex and hybrid IT landscapes.
Communication, training, and acceptance promotion
Technology alone is not enough. The introduction of passkeys should be accompanied by targeted communication and training measures. These include:
- Internal campaigns to educate users about the benefits and functionality
- Hands-on training on how to use passkeys on different devices
- FAQs and support services for all user groups
Transparent communication reduces uncertainty and promotes trust in the new technology.
Emergency concepts and operational security
Every passwordless authentication solution needs backup mechanisms for failures or device loss. These include:
- Recovery codes for one-time access
- Use of secondary devices (e.g., work and personal smartphones)
- Synchronization via the cloud for cross-device access
In addition, clear processes for support and reversal should be defined and regular security tests should be carried out.
Practical examples and success factors
Successful implementations despite legacy infrastructure
Various companies have shown that the introduction of passkeys can also be successful in complex, historically grown IT landscapes. A typical example is a medium-sized manufacturing company that had decentralized its user administration and was still using an outdated ERP and production system. By integrating a central FIDO2-enabled identity provider and using protocol translators (e.g., SAML-to-LDAP bridge), secure authentication with passkeys was implemented for web-based applications and, step by step, for internal services as well.
In another case study, a service company with a strong remote working structure implemented passkeys as the standard procedure for accessing modern SaaS solutions. Legacy systems were connected via VPN gateways, which also supported authentication via passkey.
💡 SoftGuide Infobox
What works in practice and what doesn't?
Approaches that work:
- Early involvement of stakeholders from IT, specialist departments, and management
- Pilot projects with a limited user group to validate technology and user feedback
- Clear target visions and migration paths
- Integration of IGA and IAM systems for central control
Challenges to be avoided:
- Attempting a “big bang” migration without a fallback level
- Inadequate training of end users
- Neglecting fallback scenarios in the event of device loss or authentication errors
- Unclear responsibilities in the rollout
Success factors for sustainable implementation
- Management support: Without clear support at the strategic level, many projects fail due to a lack of resources or conflicting priorities.
- Clear governance structures: The introduction of passkeys should be part of an overarching identity strategy.
- Scalable architecture: The technical infrastructure must keep pace with growing requirements and system landscapes.
- User orientation: Focusing on user experience and acceptance ensures long-term success. This includes both technical usability and transparent communication.
Conclusion: Passkeys as pioneers of secure and modern IT landscapes
The introduction of passkeys marks an important milestone on the road to passwordless authentication. Passkeys offer clear advantages in terms of security, user-friendliness, and future-proofing. Companies that take this step not only benefit from a reduced risk of phishing and credential stuffing attacks, but also from a significantly simplified user experience and lower support costs.
At the same time, it is clear that integration into existing IT landscapes is no trivial undertaking. It is particularly difficult where legacy systems are in use. These systems pose a considerable challenge due to technological limitations, missing interfaces, and security-critical legacy issues.
However, the path to successful passkey introduction is feasible. Technical solutions such as middleware, identity provider integrations, and hybrid strategies enable a phased transition without operational disruptions. From an organizational perspective, a clearly defined migration path, early involvement of relevant stakeholders, and professional change management are crucial. Training, communication, and transparent security concepts build trust among users and strengthen acceptance.
Practice shows that companies that take a structured and strategic approach can successfully implement passkeys even in complex and historically grown IT environments. Investing in modern, passwordless authentication today lays the foundation for a resilient, user-friendly, and future-oriented IT security architecture and is a decisive step toward digital resilience.