Phishing, credential stuffing, data leaks, and traditional password methods have been among the biggest vulnerabilities in digital security for years. Despite additional measures such as two-factor authentication (2FA) and password managers, passwords remain a risk. With the increasing prevalence of passkeys, a new form of authentication is coming into focus: passwordless, cryptographically secure, and easy to use.
But how secure is this technology really? This article sheds light on the technical basics, analyzes real threat scenarios, and highlights where passkeys have their greatest strengths, but also their limitations.
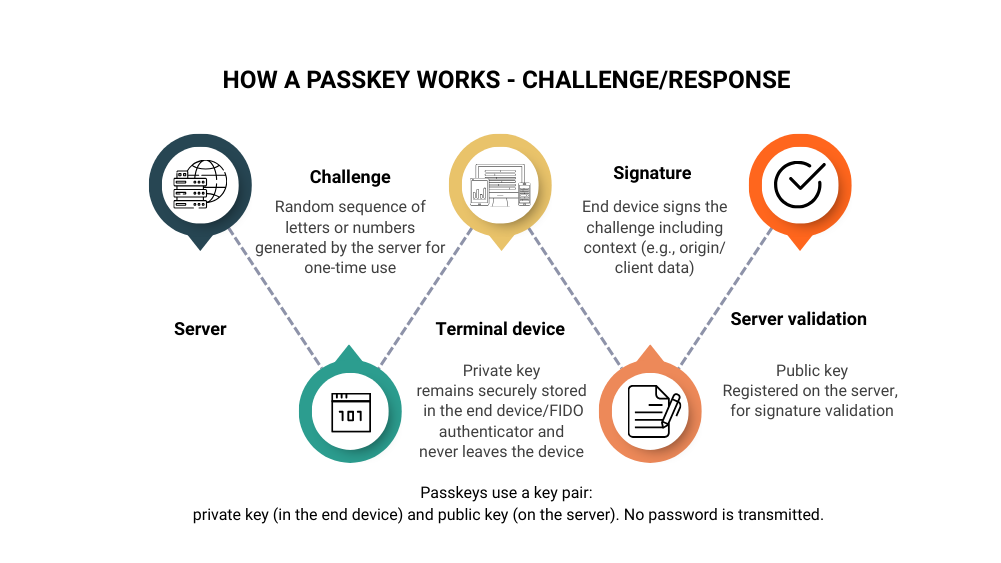
An overview of the security architecture of passkeys
Asymmetric cryptography as the foundation
Passkeys are based on a cryptographic key pair:
- The private key remains secure on the user's device (e.g., smartphone, laptop).
- The public key is stored on the server.
When logging in, the server triggers a challenge that is signed by the device using the private key. The server validates the signature with the public key without ever transferring a shared secret.
WebAuthn & FIDO2: Established security standard
The technology is based on the WebAuthn protocol and the FIDO2 standard, which were jointly developed by the FIDO Alliance and the W3C. Key security features include:
- Challenge-response mechanism instead of password transmission
- Binding to the domain for which the passkey was created
- No manual entry, no point of attack for keyloggers or social engineering
Threat model: What attacks do passkeys prevent?
Passkeys were specifically developed to eliminate the most common and consequential vulnerabilities of password-based authentication. The cryptographic architecture and the absence of shared secrets fundamentally change the target of attacks: instead of targeting people and their handling of passwords, attackers would now have to compromise the physical device. This represents a significantly higher hurdle.
The following section explains the most important threat scenarios that are effectively mitigated or completely prevented by passkeys:
Phishing attacks: Systematically prevented
Phishing is one of the most common types of attack, both in private and business environments. The aim is to trick users into entering their login details on fake websites or via email.
Why passkeys protect:
- Passkeys are tied to the web domain where they were originally generated.
- A fake login form on a phishing site cannot successfully sign the authentication request because the cryptographic challenge verifies the genuine origin.
- No password is entered, so there is nothing to steal.
Conclusion: Phishing attacks that rely on intercepting or querying passwords lose their effectiveness with passkeys.
Credential stuffing: No longer possible
In credential stuffing, attackers use stolen credentials from previous data breaches to automatically log into other accounts. This approach is particularly successful when users use the same password on multiple platforms.
Why passkeys protect:
- Passkeys are unique to each account and domain – they cannot be reused.
- There is no password that could be compromised in data leaks.
- Even if the public key is disclosed, it remains useless to attackers without the private key on the device.
Conclusion: Credential stuffing is technically impossible with passkeys, as there are no universally reusable access data.
Brute force and dictionary attacks: Cryptographically defended
With traditional password systems, attackers often try to guess access data automatically by trying out frequently used or predictable passwords.
Why passkeys protect:
- Passkeys are based on asymmetric cryptography, not on guessable character strings.
- Signature verification using the challenge-response method does not allow for any guessable patterns.
- Even with an unlimited number of attempts, a successful hit is mathematically impossible, similar to cracking a private SSL certificate.
Conclusion: Brute force attacks are impractical and economically pointless against passkeys.
Replay attacks: Structurally prevented
In replay attacks, an intercepted authentication message is sent again to gain unauthorized access.
Why passkeys protect:
- Every authentication attempt with passkeys is based on a unique, random challenge generated by the server.
- The response from the end device is valid in terms of time and context; reusing an old signature does not work.
- The validation fails because the challenge is no longer current.
Conclusion: Replay attacks are cryptographically impossible with passkeys.
Keylogging and shoulder surfing: No target for attack
Classic password attacks often target the observation or recording of password entries, for example through malware or visual surveillance.
Why passkeys protect:
- Passkeys do not require manual entry of secrets.
- Authentication is performed through biometric release, PIN, or other device unlocking methods (pattern, smart card, security key), not through keyboard entries.
- A recorded sequence cannot be repeated or transferred.
Conclusion: Keyloggers and similar tools lose their function with passkeys.
Man-in-the-middle (MitM): No transferability of keys
MitM attacks aim to tap into the communication between users and servers in order to intercept or manipulate access data.
Why passkeys protect:
- Since no password is transmitted, there is no intercepted content that can be reused.
- The challenge is domain-bound, the signature is not transferable.
- Without physical access to the device with the private key, a successful attack is not possible.
Conclusion: The attack surface for MitM attacks is reduced to a minimum.
New threat models require new defense models
Passkeys completely eliminate many of the most common attack vectors. Compared to classic password authentication or even combined MFA methods, passwordless authentication based on asymmetric cryptography offers fundamentally higher structural security.
However, the same applies here: security stands and falls with the protection of the end device and a well-thought-out backup strategy.
Risk assessment: Where are the (remaining) vulnerabilities and limitations?
Device loss & recovery
When using passkeys, the private key is stored exclusively on the end device (e.g., smartphone, tablet, or computer). If this device is lost or damaged, the key question is: How can access to the protected accounts be restored? Without a backup of the private key, for example in an encrypted cloud solution, there is a risk that access will be permanently lost.
It is therefore essential that passkey management systems support both clear recovery paths and effective backup strategies. Modern systems, such as the password managers from Apple (iCloud Keychain), Google (Passkey Keychain), Microsoft (Windows Hello), or third-party providers (e.g., 1Password, Dashlane, Bitwarden, Nordpass), usually offer synchronization and backup options in the cloud for this purpose, which can be used to recover passkeys in an emergency.
💡 SoftGuide Infobox
Brief explanation of the systems mentioned
- Apple iCloud Keychain: Synchronizes passkeys and other access data in encrypted form via the Apple cloud between all of a person's Apple devices.
- Google Passkey Keychain: Stores and synchronizes passkeys on Android devices and in Chrome via Google account, including backup in the Google cloud.
- Microsoft Windows Hello: In combination with a Microsoft account, passkeys can be secured and restored across devices.
Risk: If multiple devices are compromised, an attacker could gain access to synchronized passkeys. It is therefore crucial to secure these services with biometric authentication and device protection.
Dependence on platform providers
The infrastructure is largely shaped by large platform providers. This brings advantages in terms of integration, but also entails risks:
- Dependence on Apple, Google, etc.
- Potential lock-in effects when changing ecosystems
- Trust in the security of provider clouds required
Practicality in terms of security aspects
Part of modern security strategies
Passkeys fit perfectly into zero-trust models and modern identity architectures:
- No more implicit trust in devices or networks. Each login is checked individually.
- Can be combined with single sign-on (SSO), device trust, and policy control
- Additional security through biometric unlocking
Regulatory requirements
Passkeys support GDPR-compliant authentication because:
- No personal passwords are stored
- Authentication is unique and traceable
In certified environments such as ISO 27001, BSI Basic Protection, or TISAX (Trusted Information Security Assessment Exchange), passkeys can be a useful addition to existing measures. Passkeys were developed with data protection as a core principle and are fundamentally GDPR-compliant. They minimize the processing and storage of personal data to what is technically necessary and enable data-efficient authentication.
Experience from corporate practice
Initial companies report:
- Significantly reduced phishing attempts
Passkeys use cryptographic authentication, which largely eliminates classic attack vectors such as phishing or credential stuffing
- Fewer IT support tickets
IT departments need to reset passwords or enforce complex password rules less frequently, as passkeys no longer require traditional passwords
- Higher user satisfaction thanks to simplified logins
Facts and figures on the threat landscape
According to Verizon DBIR 2024, compromised credentials are involved in more than 70% of successful security incidents involving human influence. Most of these attacks use phishing or credential stuffing, both of which are attack methods that systematically exclude passkeys.
IBM's Cost of a Data Breach Report 2024 shows that companies with strong authentication save an average of over $1 million per data breach, particularly by preventing password theft.
According to the FIDO Alliance, companies that have introduced passkeys have been able to significantly reduce support costs, especially for password resets.
💡 SoftGuide Infobox
Facts and figures about passkeys and FIDO2
| Fact | Number / Statement | Quelle |
|
Support from major platforms |
Microsoft, Apple, and Google offer passkey integration starting with Windows 10/11, iOS/macOS 16, and Android 9+. |
Domain Factory (2025) |
|
Proportion of passwordless applications in 2025 |
According to Gartner, over 50% of enterprise applications will support passwordless authentication. |
Okta hitepaper (2023) |
|
Reduction in help desk inquiries at Microsoft |
Up to 50% fewer requests after introducing passkeys, according to Microsoft |
Microsoft Security Blog, 2022 |
|
Percentage of compromised accounts due to passwords |
83% of all data breaches are caused by stolen/weak passwords, according to Verizon DBIR 2024 |
Verizon DBIR 2024 |
|
Global distribution of FIDO2-compatible hardware |
Over 4 billion devices with FIDO2/WebAuthn support (2024 estimate) |
FIDO Alliance (2024) |
Conclusion: How secure is “passwordless” really?
Passkeys represent a significant advance in authentication technology. They eliminate key vulnerabilities of traditional password methods, particularly phishing, credential stuffing, and brute force attacks, through the use of asymmetric cryptography and standardized security protocols such as FIDO2 and WebAuthn. Security is no longer based on passwords chosen and managed by humans, but on cryptographically secured, device-bound keys.
In practice, there are clear advantages: Companies benefit from fewer security incidents, reduced IT support costs, and increased user satisfaction. Passkeys can also be easily integrated into modern security architectures and regulatory frameworks, making them particularly attractive for professional use.
At the same time, the remaining risks, especially those associated with device loss, cloud synchronization, and dependence on platform providers, must be taken seriously and addressed with well-thought-out backup strategies and device protection measures.
Overall, passkeys offer significantly higher structural security than traditional login methods and are a future-proof component of modern zero-trust strategies. For companies that want to manage digital identities securely and in a user-friendly manner, they are therefore a highly recommended step toward a passwordless future.
Further resources: Passkeys and authentication
To further deepen your understanding of passwordless authentication and the security architecture of passkeys, we recommend taking a look at various resources:
- FIDO Alliance The FIDO Alliance provides comprehensive information on passkey technologies. This ranges from basic articles to technical guides and implementation examples, as well as an interactive overview of real-world passkey implementations in companies and services.
- Passkey Central A central point of contact for the FIDO Alliance on the topic of passkeys, with a glossary, tool collections, UI kits, decision-making aids, and practical instructions for companies and IT departments.
- Industry reports – Fact-based assessment of the threat situation These reports underscore the importance of phishing-resistant methods such as passkeys and show how companies can save significant costs per data protection incident with strong authentication.
- Verizon Data Breach Investigations Report (DBIR)
- IBM Report Cost of a Data Breach - Implementation and practice
Well-founded checklists are helpful for the practical implementation of security strategies, including in conjunction with passkeys. For example, SoftGuide provides a checklist for evaluating corporate security architecture that covers key aspects such as backup, device security, recovery, cloud synchronization, and the use of modern authentication methods in a structured manner.
- Glossary of passkeys, instructions, and UI kits For developers and IT departments, the UI components, glossaries, and step-by-step instructions provided by the FIDO Alliance, such as those compiled at Passkey Central, are well worth checking out.