show 1 to 14 (of 14 software programs)
ROBERT KNOWS
 ROBERT KNOWS is the industry-neutral software for managing any inventory assets. In addition to pure inventory management, there are modules for managing contracts, licenses and for reading and monitoring network devices. A helpdesk and a rental module round off the range of functions. Inventories can be carried out using barcode scanners and tablets. Thanks to its intuitive operation without costly training, the software can be used quickly.
ROBERT KNOWS is the industry-neutral software for managing any inventory assets. In addition to pure inventory management, there are modules for managing contracts, licenses and for reading and monitoring network devices. A helpdesk and a rental module round off the range of functions. Inventories can be carried out using barcode scanners and tablets. Thanks to its intuitive operation without costly training, the software can be used quickly.
Inventory management / Contracts / Licenses / Helpdesk
 ROBERT KNOWS is the industry-neutral software for managing any inventory assets. In addition to pure inventory management, there are modules for managing contracts, licenses and for reading and monitoring network devices. A helpdesk and a rental module round off the range of functions. Inventories can be carried out using barcode scanners and tablets. Thanks to its intuitive operation without costly training, the software can be used quickly.
ROBERT KNOWS is the industry-neutral software for managing any inventory assets. In addition to pure inventory management, there are modules for managing contracts, licenses and for reading and monitoring network devices. A helpdesk and a rental module round off the range of functions. Inventories can be carried out using barcode scanners and tablets. Thanks to its intuitive operation without costly training, the software can be used quickly.
QSEC - GRC/ISMS, ISO 27001/BSI standard- IT protection, B3S and data protection
 QSEC is an integrated management system that provides the management with decisions based on transparency and facts and supplies the corporate risk management with important decision basics from the operative risk management. The implementation of. the Compliance, of Information Security Management according to the requirements of ISO 27001, BSI standard (IT-Grundschutz), B3S Risk Management anddata protection according to GDPR Data Protection according to GDPR In addition, a wide range of other requirements ...
QSEC is an integrated management system that provides the management with decisions based on transparency and facts and supplies the corporate risk management with important decision basics from the operative risk management. The implementation of. the Compliance, of Information Security Management according to the requirements of ISO 27001, BSI standard (IT-Grundschutz), B3S Risk Management anddata protection according to GDPR Data Protection according to GDPR In addition, a wide range of other requirements ...
GRC, ISMS, risk management, IMS, IKS, and data protection - "All-in-one"!
 QSEC is an integrated management system that provides the management with decisions based on transparency and facts and supplies the corporate risk management with important decision basics from the operative risk management. The implementation of. the Compliance, of Information Security Management according to the requirements of ISO 27001, BSI standard (IT-Grundschutz), B3S Risk Management anddata protection according to GDPR Data Protection according to GDPR In addition, a wide range of other requirements ...
QSEC is an integrated management system that provides the management with decisions based on transparency and facts and supplies the corporate risk management with important decision basics from the operative risk management. The implementation of. the Compliance, of Information Security Management according to the requirements of ISO 27001, BSI standard (IT-Grundschutz), B3S Risk Management anddata protection according to GDPR Data Protection according to GDPR In addition, a wide range of other requirements ...
myPARM - Multi-project management software
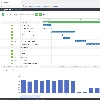 myPARM PM is a strategic, process-oriented multi-project management software with Gantt and WBS, time recording, budgeting, resource planning, invoicing, risk and opportunity management. myPARM RFS is a risk-based management/leadership system with balanced scorecard, portfolio management, programme management and controlling options for operational, tactical and strategic management levels.
myPARM PM is a strategic, process-oriented multi-project management software with Gantt and WBS, time recording, budgeting, resource planning, invoicing, risk and opportunity management. myPARM RFS is a risk-based management/leadership system with balanced scorecard, portfolio management, programme management and controlling options for operational, tactical and strategic management levels.
Multi-project management and PPM software
 myPARM PM is a strategic, process-oriented multi-project management software with Gantt and WBS, time recording, budgeting, resource planning, invoicing, risk and opportunity management. myPARM RFS is a risk-based management/leadership system with balanced scorecard, portfolio management, programme management and controlling options for operational, tactical and strategic management levels.
myPARM PM is a strategic, process-oriented multi-project management software with Gantt and WBS, time recording, budgeting, resource planning, invoicing, risk and opportunity management. myPARM RFS is a risk-based management/leadership system with balanced scorecard, portfolio management, programme management and controlling options for operational, tactical and strategic management levels.
BIC GRC - Integrated and scalable GRC solutions for all use cases
 The success of innovative organizations can be sustainably increased through the digitalization of GRC processes.
We make this possible with our BIC GRC software, which offers our customers flexible and adaptable custom solutions or ready-to-use standard solutions:
BIC Enterprise Risk
BIC Internal Control
BIC Corporate Sustainability
BIC Information Security
BIC Business Continuity
BIC Data Protection
BIC Internal Audit
many other GRC use cases (Compliance, DORA and NIS-2)...
The success of innovative organizations can be sustainably increased through the digitalization of GRC processes.
We make this possible with our BIC GRC software, which offers our customers flexible and adaptable custom solutions or ready-to-use standard solutions:
BIC Enterprise Risk
BIC Internal Control
BIC Corporate Sustainability
BIC Information Security
BIC Business Continuity
BIC Data Protection
BIC Internal Audit
many other GRC use cases (Compliance, DORA and NIS-2)...
Ready-to-use solutions for the future-proof digitalization of your GRC processes
 The success of innovative organizations can be sustainably increased through the digitalization of GRC processes.
We make this possible with our BIC GRC software, which offers our customers flexible and adaptable custom solutions or ready-to-use standard solutions:
BIC Enterprise Risk
BIC Internal Control
BIC Corporate Sustainability
BIC Information Security
BIC Business Continuity
BIC Data Protection
BIC Internal Audit
many other GRC use cases (Compliance, DORA and NIS-2)...
The success of innovative organizations can be sustainably increased through the digitalization of GRC processes.
We make this possible with our BIC GRC software, which offers our customers flexible and adaptable custom solutions or ready-to-use standard solutions:
BIC Enterprise Risk
BIC Internal Control
BIC Corporate Sustainability
BIC Information Security
BIC Business Continuity
BIC Data Protection
BIC Internal Audit
many other GRC use cases (Compliance, DORA and NIS-2)...
Z1 SecureHub
 With Z1 SecureHub, you can transfer large files securely and in compliance with the EU General Data Protection Regulation. Whether videos, presentations or databases, files can be easily sent and received via your own Z1 SecureHub. All data is stored in your own infrastructure.
With Z1 SecureHub, you can transfer large files securely and in compliance with the EU General Data Protection Regulation. Whether videos, presentations or databases, files can be easily sent and received via your own Z1 SecureHub. All data is stored in your own infrastructure.
Exchange large files spontaneously, easily and securely in compliance with the GDPR
 With Z1 SecureHub, you can transfer large files securely and in compliance with the EU General Data Protection Regulation. Whether videos, presentations or databases, files can be easily sent and received via your own Z1 SecureHub. All data is stored in your own infrastructure.
With Z1 SecureHub, you can transfer large files securely and in compliance with the EU General Data Protection Regulation. Whether videos, presentations or databases, files can be easily sent and received via your own Z1 SecureHub. All data is stored in your own infrastructure.
Cryptshare
 Exchange information and large files securely, easily and traceably by email. Cryptshare enhances your existing e-mail system with security, administrative control, traceability and the ability to exchange files of unlimited size. In order to live up to our slogan "Making e-mail better", we place particular emphasis on user-friendliness, because software only makes financial and security sense if it is well accepted and popular with users. Therefore, there is no need for software installations, user accounts, procurement of certificates or exchange of public keys on the part of the end user ...
Exchange information and large files securely, easily and traceably by email. Cryptshare enhances your existing e-mail system with security, administrative control, traceability and the ability to exchange files of unlimited size. In order to live up to our slogan "Making e-mail better", we place particular emphasis on user-friendliness, because software only makes financial and security sense if it is well accepted and popular with users. Therefore, there is no need for software installations, user accounts, procurement of certificates or exchange of public keys on the part of the end user ...
Sending large files - exchanging e-mails securely
 Exchange information and large files securely, easily and traceably by email. Cryptshare enhances your existing e-mail system with security, administrative control, traceability and the ability to exchange files of unlimited size. In order to live up to our slogan "Making e-mail better", we place particular emphasis on user-friendliness, because software only makes financial and security sense if it is well accepted and popular with users. Therefore, there is no need for software installations, user accounts, procurement of certificates or exchange of public keys on the part of the end user ...
Exchange information and large files securely, easily and traceably by email. Cryptshare enhances your existing e-mail system with security, administrative control, traceability and the ability to exchange files of unlimited size. In order to live up to our slogan "Making e-mail better", we place particular emphasis on user-friendliness, because software only makes financial and security sense if it is well accepted and popular with users. Therefore, there is no need for software installations, user accounts, procurement of certificates or exchange of public keys on the part of the end user ...
audatis MANAGER - Data protection management software
 Data processing agreements, records of processing activities, TOMs, employee training with certificates - the EU General Data Protection Regulation has many requirements - audatis® Manager supports you in dealing with them and ensures that you are on the safe side. The web-based software solution for data protection is multilingual and multi-client capable and is optionally available with industry-specific templates for the register of processing activities.
Data processing agreements, records of processing activities, TOMs, employee training with certificates - the EU General Data Protection Regulation has many requirements - audatis® Manager supports you in dealing with them and ensures that you are on the safe side. The web-based software solution for data protection is multilingual and multi-client capable and is optionally available with industry-specific templates for the register of processing activities.
Data protection management software and e-learning from experts: simply use it online!
 Data processing agreements, records of processing activities, TOMs, employee training with certificates - the EU General Data Protection Regulation has many requirements - audatis® Manager supports you in dealing with them and ensures that you are on the safe side. The web-based software solution for data protection is multilingual and multi-client capable and is optionally available with industry-specific templates for the register of processing activities.
Data processing agreements, records of processing activities, TOMs, employee training with certificates - the EU General Data Protection Regulation has many requirements - audatis® Manager supports you in dealing with them and ensures that you are on the safe side. The web-based software solution for data protection is multilingual and multi-client capable and is optionally available with industry-specific templates for the register of processing activities.
CRISAM® GRC | Data Protection Management System
 Thanks to the intuitive user interface, data protection management with CRISAM® is easy to handle for both data controllers and processors. CRISAM® supports the legally compliant recording of company content in the area of data protection. The efficient solution grows with your requirements and can be flexibly adapted to your needs. CRISAM® meets the requirements of the European General Data Protection Regulation and is audit-proof.
Thanks to the intuitive user interface, data protection management with CRISAM® is easy to handle for both data controllers and processors. CRISAM® supports the legally compliant recording of company content in the area of data protection. The efficient solution grows with your requirements and can be flexibly adapted to your needs. CRISAM® meets the requirements of the European General Data Protection Regulation and is audit-proof.
Data protection management EU GDPR-compliant
 Thanks to the intuitive user interface, data protection management with CRISAM® is easy to handle for both data controllers and processors. CRISAM® supports the legally compliant recording of company content in the area of data protection. The efficient solution grows with your requirements and can be flexibly adapted to your needs. CRISAM® meets the requirements of the European General Data Protection Regulation and is audit-proof.
Thanks to the intuitive user interface, data protection management with CRISAM® is easy to handle for both data controllers and processors. CRISAM® supports the legally compliant recording of company content in the area of data protection. The efficient solution grows with your requirements and can be flexibly adapted to your needs. CRISAM® meets the requirements of the European General Data Protection Regulation and is audit-proof.
FieldShield
 IRI FieldShield® is powerful and cost-effective software for data discovery and data masking of PII in structured and semi-structured sources, onsite or in the cloud, static or streaming. The FieldShield utilities in Eclipse are used to profile and de-identify data at rest (static data masking) and the FieldShield SDK is used to secure data in motion (dynamic data masking).
IRI FieldShield® is powerful and cost-effective software for data discovery and data masking of PII in structured and semi-structured sources, onsite or in the cloud, static or streaming. The FieldShield utilities in Eclipse are used to profile and de-identify data at rest (static data masking) and the FieldShield SDK is used to secure data in motion (dynamic data masking).
Powerful and cost-effective software for data recognition and masking .
 IRI FieldShield® is powerful and cost-effective software for data discovery and data masking of PII in structured and semi-structured sources, onsite or in the cloud, static or streaming. The FieldShield utilities in Eclipse are used to profile and de-identify data at rest (static data masking) and the FieldShield SDK is used to secure data in motion (dynamic data masking).
IRI FieldShield® is powerful and cost-effective software for data discovery and data masking of PII in structured and semi-structured sources, onsite or in the cloud, static or streaming. The FieldShield utilities in Eclipse are used to profile and de-identify data at rest (static data masking) and the FieldShield SDK is used to secure data in motion (dynamic data masking).
CellShield
 IRI CellShield to find and protect sensitive data (PII) in multiple Excel® spreadsheets: CellShield is the only full-featured, professional data discovery, masking and auditing package for Excel 2010, 2013, 2016 and 2019 (plus Office 365) workbooks on your LAN. CellShield exceeds the security and scope of a single password by combining and automating additional features.
IRI CellShield to find and protect sensitive data (PII) in multiple Excel® spreadsheets: CellShield is the only full-featured, professional data discovery, masking and auditing package for Excel 2010, 2013, 2016 and 2019 (plus Office 365) workbooks on your LAN. CellShield exceeds the security and scope of a single password by combining and automating additional features.
Reporting & masking of PII in Microsoft Excel® spreadsheets
 IRI CellShield to find and protect sensitive data (PII) in multiple Excel® spreadsheets: CellShield is the only full-featured, professional data discovery, masking and auditing package for Excel 2010, 2013, 2016 and 2019 (plus Office 365) workbooks on your LAN. CellShield exceeds the security and scope of a single password by combining and automating additional features.
IRI CellShield to find and protect sensitive data (PII) in multiple Excel® spreadsheets: CellShield is the only full-featured, professional data discovery, masking and auditing package for Excel 2010, 2013, 2016 and 2019 (plus Office 365) workbooks on your LAN. CellShield exceeds the security and scope of a single password by combining and automating additional features.
DarkShield
 With IRI DarkShield, you can classify, find and delete or otherwise mask sensitive information in various structured, semi-structured and unstructured sources, including: text, PDF and MS Office documents, Parquet and image files, relational and NoSQL collections, and even faces. Whether the PII is on your desktop or anywhere on your network, DarkShield protects it!...
With IRI DarkShield, you can classify, find and delete or otherwise mask sensitive information in various structured, semi-structured and unstructured sources, including: text, PDF and MS Office documents, Parquet and image files, relational and NoSQL collections, and even faces. Whether the PII is on your desktop or anywhere on your network, DarkShield protects it!...
Recognize, deploy and delete PII in Dark Data
 With IRI DarkShield, you can classify, find and delete or otherwise mask sensitive information in various structured, semi-structured and unstructured sources, including: text, PDF and MS Office documents, Parquet and image files, relational and NoSQL collections, and even faces. Whether the PII is on your desktop or anywhere on your network, DarkShield protects it!...
With IRI DarkShield, you can classify, find and delete or otherwise mask sensitive information in various structured, semi-structured and unstructured sources, including: text, PDF and MS Office documents, Parquet and image files, relational and NoSQL collections, and even faces. Whether the PII is on your desktop or anywhere on your network, DarkShield protects it!...
humbee - the cloud workplace
 Free yourself from the search: work in the process instead of the chaos. Do your employees spend valuable time searching for information from emails, file systems, CRM and DMS tools? humbee puts an end to this inefficient chaos. As a holistic cloud platform, humbee combines DMS, collaboration, CRM and process automation - all consistently aligned with the principle of process-based working. This means that all documents, tasks, emails and coordination relating to a customer, object or order are centrally located in one place - the process ...
Free yourself from the search: work in the process instead of the chaos. Do your employees spend valuable time searching for information from emails, file systems, CRM and DMS tools? humbee puts an end to this inefficient chaos. As a holistic cloud platform, humbee combines DMS, collaboration, CRM and process automation - all consistently aligned with the principle of process-based working. This means that all documents, tasks, emails and coordination relating to a customer, object or order are centrally located in one place - the process ...
The digital cloud workplace for DMS, CRM, processes and collaboration in the process.
 Free yourself from the search: work in the process instead of the chaos. Do your employees spend valuable time searching for information from emails, file systems, CRM and DMS tools? humbee puts an end to this inefficient chaos. As a holistic cloud platform, humbee combines DMS, collaboration, CRM and process automation - all consistently aligned with the principle of process-based working. This means that all documents, tasks, emails and coordination relating to a customer, object or order are centrally located in one place - the process ...
Free yourself from the search: work in the process instead of the chaos. Do your employees spend valuable time searching for information from emails, file systems, CRM and DMS tools? humbee puts an end to this inefficient chaos. As a holistic cloud platform, humbee combines DMS, collaboration, CRM and process automation - all consistently aligned with the principle of process-based working. This means that all documents, tasks, emails and coordination relating to a customer, object or order are centrally located in one place - the process ...
HITGuard GRC
 HITGuard is revolutionizing the world of audit, data protection, incident, risk and compliance management. With its intuitive user interface and intelligent features, it is the ideal tool for any organization to ensure effective and transparent governance. It provides everything you need to optimize your compliance and risk management processes and ensure that your data and systems are secure and protected.
HITGuard is revolutionizing the world of audit, data protection, incident, risk and compliance management. With its intuitive user interface and intelligent features, it is the ideal tool for any organization to ensure effective and transparent governance. It provides everything you need to optimize your compliance and risk management processes and ensure that your data and systems are secure and protected.
Clear audit, data protection, incident, risk and compliance management - cloud/on-prem
 HITGuard is revolutionizing the world of audit, data protection, incident, risk and compliance management. With its intuitive user interface and intelligent features, it is the ideal tool for any organization to ensure effective and transparent governance. It provides everything you need to optimize your compliance and risk management processes and ensure that your data and systems are secure and protected.
HITGuard is revolutionizing the world of audit, data protection, incident, risk and compliance management. With its intuitive user interface and intelligent features, it is the ideal tool for any organization to ensure effective and transparent governance. It provides everything you need to optimize your compliance and risk management processes and ensure that your data and systems are secure and protected.
audatis MANAGER - Whistleblower system
 To meet the requirements of the EU Whistleblowing Directive and the German Whistleblower Protection Act (HinSchG), we offer an optional module in audatis MANAGER as a whistleblower system. With the whistleblower system, you can receive (anonymous) reports as the person responsible and communicate with the whistleblower (anonymously) via an encrypted channel.
To meet the requirements of the EU Whistleblowing Directive and the German Whistleblower Protection Act (HinSchG), we offer an optional module in audatis MANAGER as a whistleblower system. With the whistleblower system, you can receive (anonymous) reports as the person responsible and communicate with the whistleblower (anonymously) via an encrypted channel.
Set up your own confidential (and anonymous) whistleblowing system.
 To meet the requirements of the EU Whistleblowing Directive and the German Whistleblower Protection Act (HinSchG), we offer an optional module in audatis MANAGER as a whistleblower system. With the whistleblower system, you can receive (anonymous) reports as the person responsible and communicate with the whistleblower (anonymously) via an encrypted channel.
To meet the requirements of the EU Whistleblowing Directive and the German Whistleblower Protection Act (HinSchG), we offer an optional module in audatis MANAGER as a whistleblower system. With the whistleblower system, you can receive (anonymous) reports as the person responsible and communicate with the whistleblower (anonymously) via an encrypted channel.show 1 to 14 (of 14 software programs)
1